Phishing

Phishing is an unsolicited message (email, text, or phone) that appears to be from a trusted entity but is actually from someone attempting to trick you into divulging private information such as passwords and financial account numbers. Often they install malware on your device. These messages encourage you to click a link that takes you to a fraudulent website where you are asked to log in or submit private information where a scammer collects it. Sometimes they encourage you to open an attachment. Your stolen information is used to commit identity theft, withdraw funds from your financial accounts, or access password-protected sites as you. Malware infestations can bring your device to a halt, damage your files, steal information from it, or install ransomware. Full EKU IT Phishing Training PowerPoint (PDF)
If you receive a message that you believe is suspicious, don't click or respond to other bait. You can forward messages to EKU IT (spam@eku.edu).
What happens when you forward an email to spam@eku.edu?
- We look at each message.
- If the message is a scammer trying to impersonate someone at the university (Sender: David McFaddin <d-mcfaddin[at]gmail.com>, we block that email address. We also reach out to those who received or interacted with the message alerting them.
- If the message is legitimate (less than 5% of the time), we respond by letting the person who sent it know that it is legitimate.
What does EKU do to combat phishing from emails?
EKU IT has many safety measures put into place, but YOU (the user) are our best line of defense! Be suspicious, don't be bullied or rushed, and if you see something, report it!
- Spam Filter. EKU's spam filter takes out a lot of the spam and phishing before it ever reaches your inbox.
- [EXTERNAL] Email Tag. This alerts users that the email did not originate from an EKU email address.
- Multifactor/Two-Factor Authentication. Asking users to verify they are who they say they are, helps too.
- Safe Links and Attachments. If a link or attachment is known to be malicious, they are automatically blocked.
- Impersonation Settings Policy. This setting is enabled at the university C-level (EKU President, VPs) to protect users from email spoofing and spear phishing, and whaling that comes along with it. Email spoofing is when someone creates a fake email, for example, in Gmail, that has a familiar name but uses the Gmail email account and is sent to staff reports. These spoofed messages usually ask the sender to purchase gift cards, take pictures of the codes on the cards, and return the images to the sender's email address. Enabling the impersonation setting will automatically redirect all such emails to our spam account, bypassing staff.
Even with all that and extra support on the back-end from our email source-Microsoft-phishing still occurs here. If a person is phished, hacked, scammed--it can do a lot of damage. There are no easy fixes for that except educating the users.
How to Recognize Phishing
- Look at the sender's address. Hover over or double-click to open it. Is it the same email as what you see displayed? If no, the message is probably fraudulent or malicious. If yes, do you know the sender, and are they family, friends, or co-workers? How have they contacted you--work email or social media or text or phone calls? Scammers have access to families, friends, and co-workers they have successfully attacked or from your social media (or other internet sites) or your address book.
- Is there an attachment or link? If so, were you expecting this from that sender? If yes, it should be safe to open. If you were not expecting a link or attachment, send a message to them with another method to check. For example, if the text you a link or attachment, email them about it before you click. Don't use the same manner (text back) because if their account is hacked, you will simply reach the hacker. Is the link real? If you hover over it, what do you see? Is the link shortened--never trust these!
- Are they asking for immediate help or actions be taken (giving personal information, performing a risky action)? If yes, stop and slow down. Reach out (with a second method) and ask. Don't be rushed into doing anything!
- Are they obviously after passwords, financial information, your identity information, or money? If yes, it is phishing.
- Are they itching one or more of these desires: urgency, desire to please, greed, curiosity, complacency, or fear? Then it is probably phishing.
- Do they have spelling and grammar errors? Offer things that sound too good to be true? Then it is probably phishing.
- There are other giveaways that an email could be phishing: They use an official logo or signature. The subject of the email is unprofessional.
Example EKU Phishing Messages [EKU Phishing Alert Page]
Example 1:
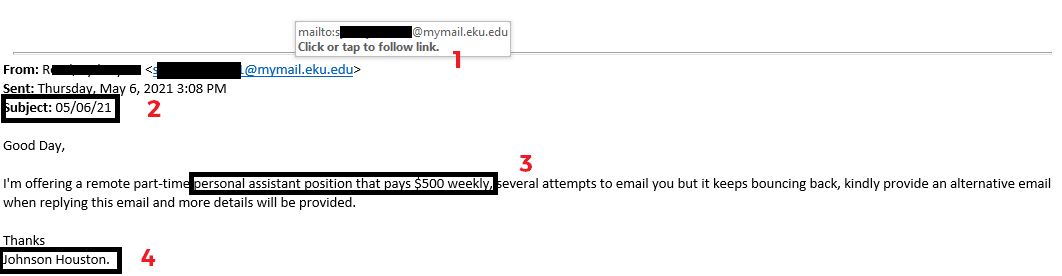
Issues:
- The email is originating from an @mymail.eku.edu, which is designated for EKU students.
- The subject is unprofessional and makes no sense. It is simply the date the email was sent.
- This is the golden rule: "If it's too good to be true, it usually is."
- The name in the signature does NOT match the student in the From line.
Example 2:
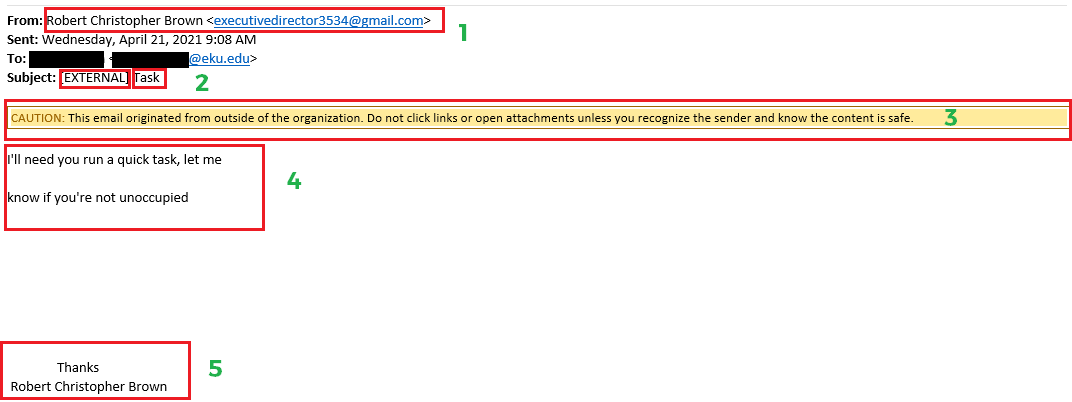
Issues:
- The sender is trying to spoof an real person at EKU at the executive level, using a Gmail address.
- The subject has the [EXTERNAL] tag, which means the email account is not one from EKU and the subject is unprofessional and makes no sense.
- This caution line is another alert that the email is from outside EKU.
- This is poor grammar and form.
- The signature is also bad form and if this person knew the recipient on this level they probably wouldn't sign with their full name.
Example 3:
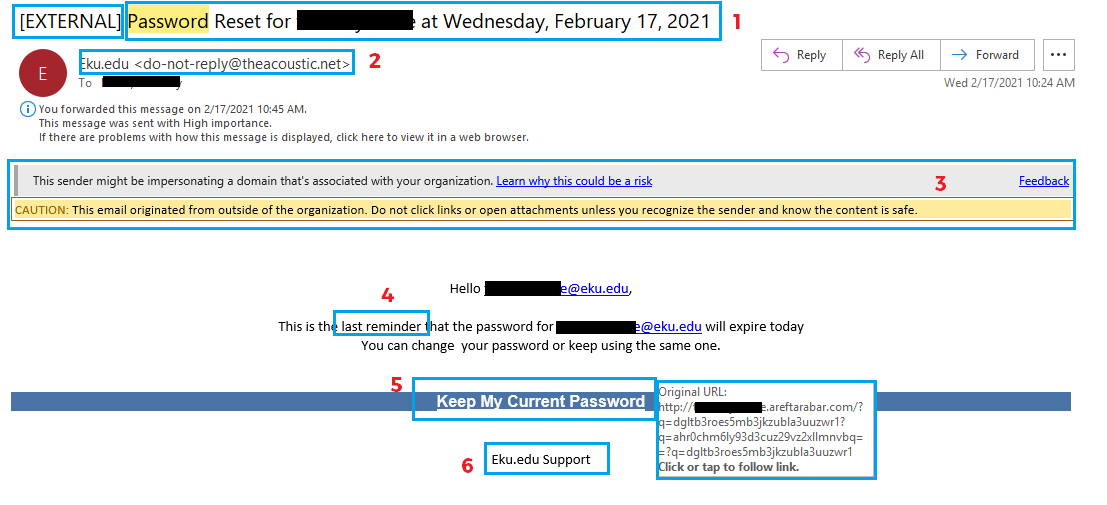
Issues:
- Subject has the [EXTERNAL] tag and, even though the subject line itself isn't horrible, it is trying to "pretent" it is originating from EKU IT and we would never solicit a user to change their password this way.
- The sender says Eku.edu but the actual address is a .net account. And we are EKU, not Eku.
- Warning messages.
- Trying to "rush" the user into performing a risky action--click the link and give up their credentials.
- The link reads 'Keep My Current Password' but if you hove over the link you can see that it goes to a non-EKU .com address.
- The footer information makes no sense because EKU IT is not Eku.edu Support. And we are EKU, not Eku.
Test Yourself
Take a look at the email below and see if you can find all the issues (answers below):
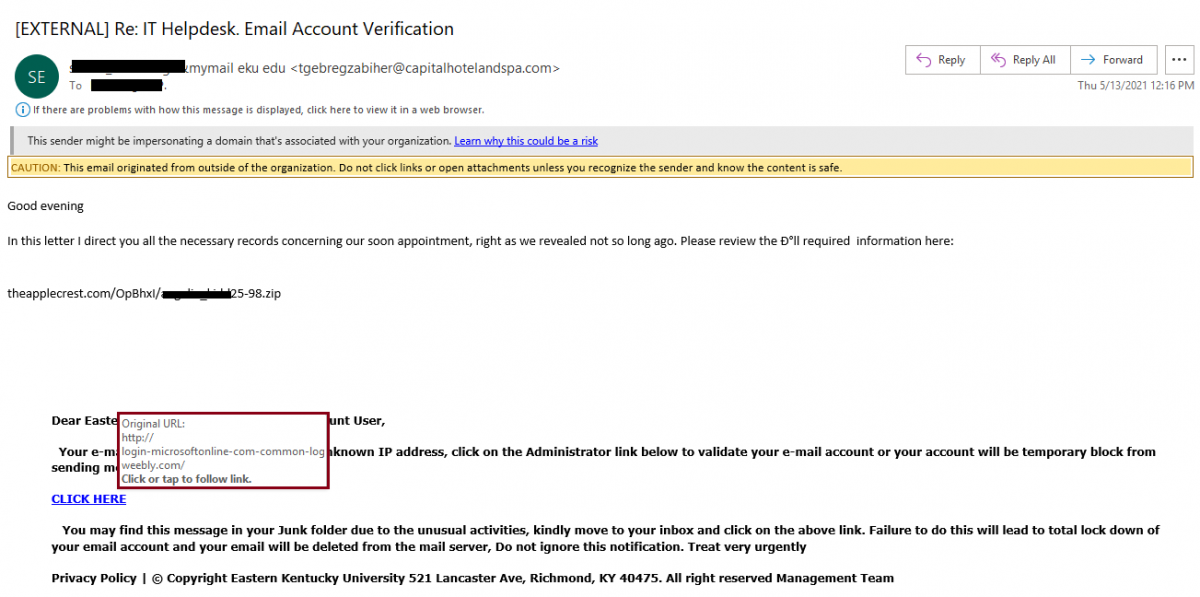
Answers:
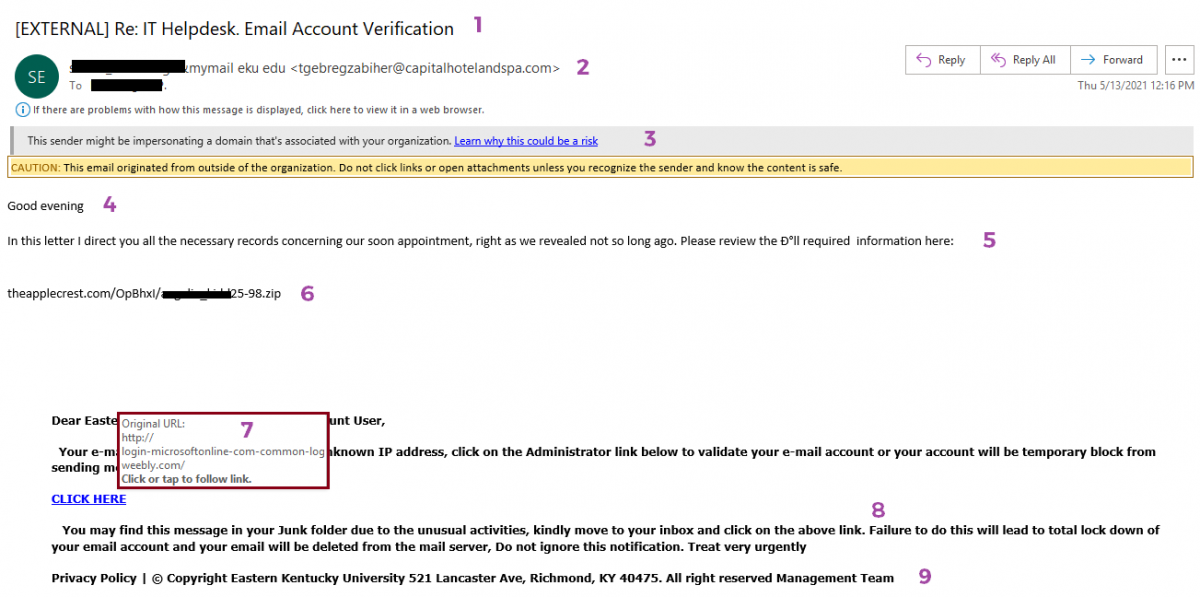
Issues:
- The subject has the [EXTERNAL] tag and poorly written subject line.
- The email is from a mymail.eku.edu (EKU student) but no @ sign but the actual address is a .com.
- Warning messages.
- Poor salutation. Missing comma.
- Bad grammar.
- Has a .zip attachment.
- The 'CLICK HERE' link, if you hover over it, mentions Microsoft, but is actually a weebly[dot]com website which is a website where anyone can create a free website so it is often used by scammres.
- Bad grammar.
- The footer doesn't make any sense: no copyright date and what is the 'Management Team'?
Remember...
- You (the user) are our best line of defense!
- Be suspicious of any unexpected/unsolicited emails, text messages, and phone calls.
- Don't be bullied or rushed into reacting without thinking first.
- Be more suspicious if passwords, financial information, your identy, or money are involved.
- If you see something, report it!