Phishing

Phishing email messages, websites, and phone calls are designed to steal money and/or information. Cybercriminals install malware on your computer or steal personal information off of your computer. Legitimate companies will never ask for your personal information (passwords, usernames, social security numbers, etc.)
Hundreds of phishing attempts are stopped by the filters and firewall currently in place at EKU. Occasionally one will make it though to employee and/or student email inbox.
All official IT notices come from the EKU email address: IT.NOTICE@eku.edu and are branded with the Keen Johnson logo at the bottom of the email.
We post phishing alerts on our X account and online.
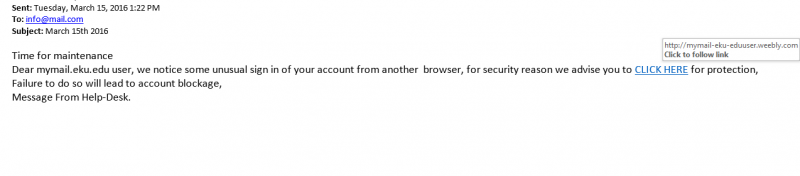
What does a phishing email message look like?
Here is an example of what a phishing scam in an email message might look like.
How to recognize phishing attempts
- Generic greetings. Many spoof emails begin with a general greeting, such as: "Dear Company member." If you do not see your first and last name, be suspicious and do not click on any links or button.
- A fake sender's address. A spoof email may include a forged email address in the "From" field. This field is easily altered.
- A false sense of urgency. Many spoof emails try to deceive you with the threat that your account is in jeopardy if you don't update it ASAP. They may also state that an unauthorized transaction has recently occurred on your account, or claim they are updating accounts and need information fast.
- Fake links. Always check where a link is going before you click. Move your mouse over it and look at the URL in your browser or email status bar. A fraudulent link is dangerous. If you click on one, it could:
- Direct you to a spoof website that tries to collect your personal data.
- Install spyware on your system. Spyware is an application that can enable a hacker to monitor your actions and steal any passwords or credit card numbers you type online.
- Cause you to download a virus that could disable your computer.
- Emails that appear to be websites. Some emails will look like a website in order to get you to enter personal information. Legitimate companies never ask for personal information in an email.
- Deceptive URLs.
- If you see an @ sign in the middle of a URL, there's a good chance this is a spoof. Legitimate companies use a domain name (e.g. https://www. company. com).
- Even if a URL contains the name of the company, it may not be the real site. Examples of deceptive URLs include: www. ebaysecure. com, www. paypa1. com, www. secure-paypal. com, and www. ebaypalnet. com.
- Always log in to a companies site by opening a new web browser.
- Never log in to site from a link in an email.
- Misspellings and bad grammar. Spoof emails often contain misspellings, incorrect grammar, missing words, and gaps in logic. Mistakes also help fraudsters avoid spam filters.
- Unsafe sites. The term "https" should always precede any website address where you enter personal information. The "s" stands for secure. If you don't see "https," you're not in a secure web session, and you should not enter data.
- Pop-up boxes. Legitimate companies will never use pop-ups as they are not secure.
- Attachments. Like fake links, attachments are frequently used in spoof emails and are dangerous. Never click on an attachment if you are unsure of its origin. It could cause you to download spyware or a virus.
- Beware of phishing phone calls
- Never give your user names and/or passwords over the telephone to an unsolicited caller
- Treat all unsolicited phone calls as Phishing attempts
What to do if you Receive a Phishing Email Attempt
Protect Yourself
Here are some additional ways to protect you:
- Never provide your personal information to an unsolicited request, whether it is over the phone or over the Internet.
- If you believe the contact may be legitimate, contact the financial institution yourself.
- Never provide your password or PIN number over the phone or in response to an
unsolicited Internet request. - Review account statements regularly to ensure all charges are correct.
Additional information about Phishing
Antiphishing.org
Using Caution with Email Attachments
Avoiding Social Engineering and Phishing Attacks
For information about other data security issues, see this support article.